You can prevent web services from specific, common SQL injection threats. This inspects the request message for the specific patterns of characters or keywords that are associated with these potential SQL injection attacks.
Configure the assertion as below:
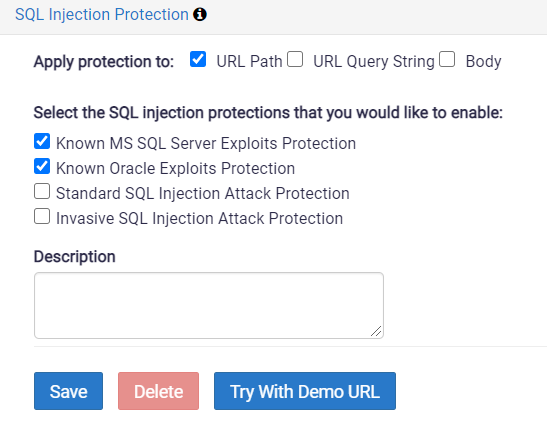
- Apply Protection to:
Specify where to apply the protection:- URL Path: Select this to protect the URL Path.
- URL Query String: Select this to protect the query parameters in the URL.
- Body: Select this to protect the body of the message.
- Known MS SQL Server Exploits Protection
Block messages that contain patterns recognized as potential MS SQL Server exploits. - Known Oracle Exploit Protection
Block messages that contain patterns recognized as potential Oracle SQL exploits - Standard SQL Attack Protection
Block messages which contain a single-quote (‘), a hash mark (#), or string (–) inside the element text or CDATA section (the characters are permitted in message attributes). - Invasive SQL Attack Protection
Block messages that contain a single-quote (‘), a hash mark (#), or string (–) anywhere within the message.
